Member-only story
Restricting access to AWS based on source IP and its considerations
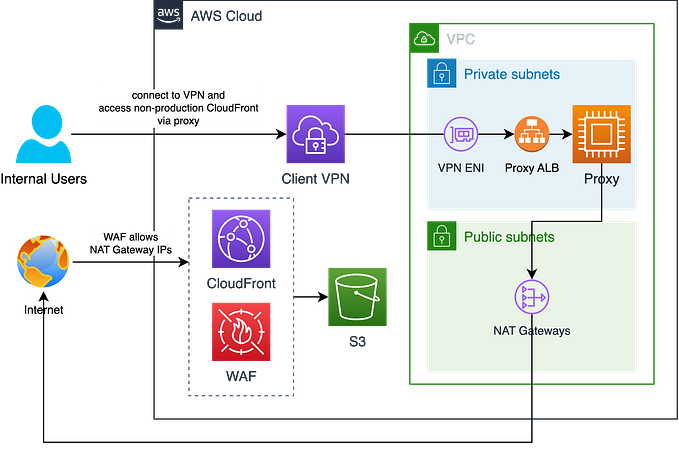
Some organisations may require you to restrict AWS access for all or a subset of users to only the specified IP ranges as part of the security policy or for other reasons. Typically, these IP ranges are the organisation’s IP addresses. This AWS documentation shows how we can craft a simple IAM policy to deny all AWS actions in the account when the request is not from the specified IP ranges.
https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_examples_aws_deny-ip.html
Example:
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"NotIpAddress": {
"aws:SourceIp": [
"<CIDR range 1>",
"<CIDR range 2>"
]
},
"Bool": {"aws:ViaAWSService": "false"}
}
}
}This IAM policy is attached to a user or role that will be assumed via single sign on.
Let’s look at some considerations when implementing this policy.
aws:SourceIp does not support private network
At the point of writing this blog, aws:SourceIp does not support private IP addresses. You should only specify public IP addresses in the IAM policy. If you specify private IP addresses, it will not work.